WEB
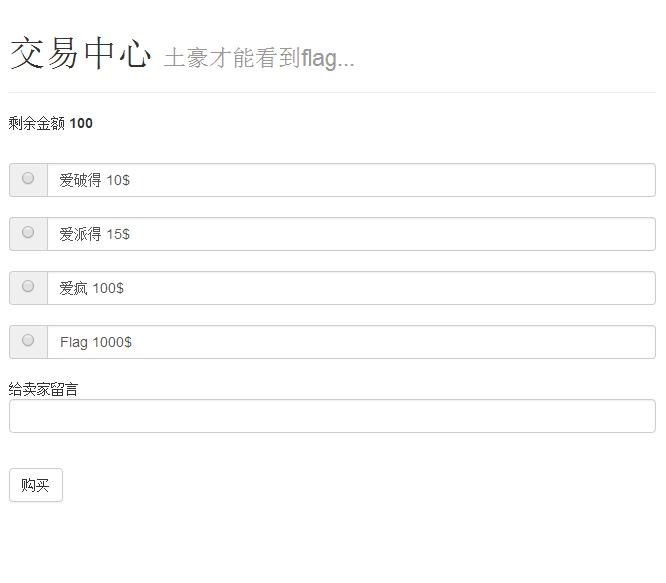
WEB1 交易中心,你能买到FLAG吗?
提供了源码下载
-
分析源码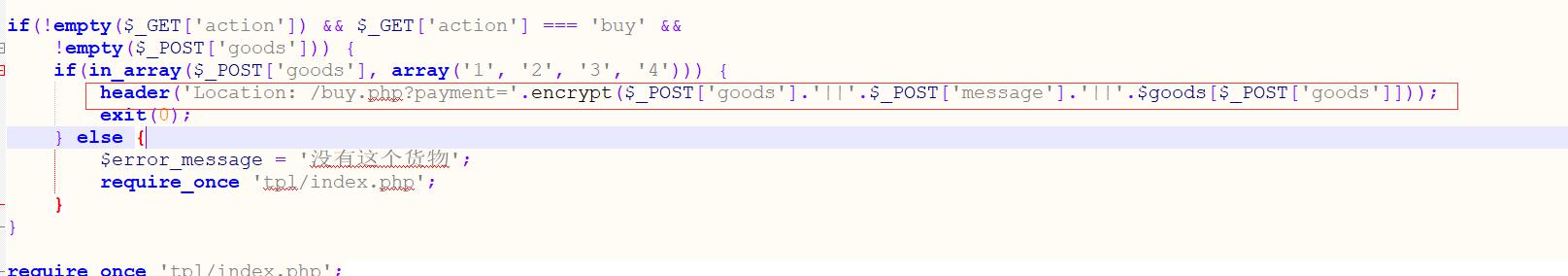
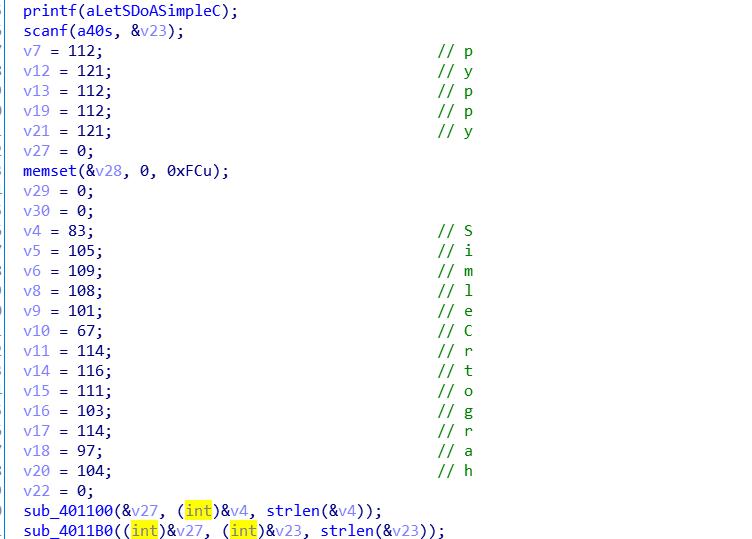
POST三个参数 并且通过||进行拼接 这样最后的payment应该为goods||message||goods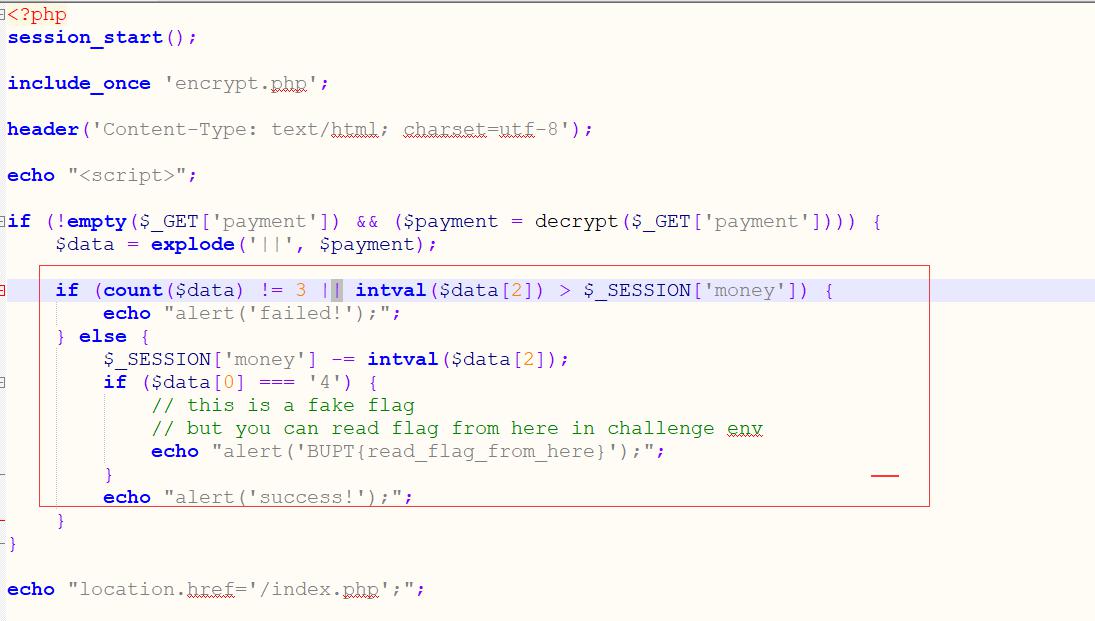
了解到intval()函数功能1、参数一定是数字否则会报错,2、如果是数字那一定是整数,如果有小点,那会省略掉,3,强调参数可以有“-”值。4、参数第一位不应为0开头,不然会自动转换十进制。
而参数message可控 所以可以想出让intval转换停在message所传值后面利用既然是利用||分割进行转换 所以这里传值时打乱原有的||分割使payment再次被分割时出现非数字使之停止
构造 直接在POST写入
所以构造payload:goods=4&message=40|(此处为当时测试所用值)&goods=1000
所得之后的数据为4||40|||1000 分割后会导致第三数据的1000变为|1000
提交得到flag
RE
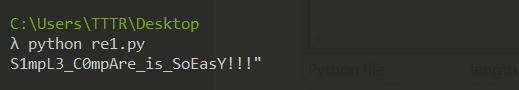
Re1
运行程序了解程序流程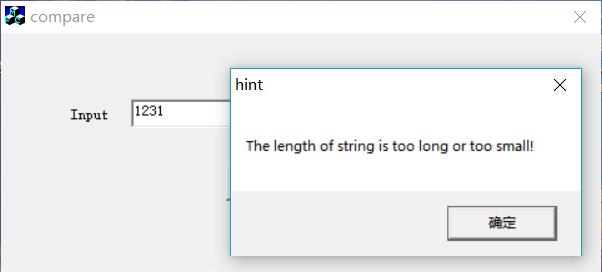
进行了长度判断
不是很会RE 发现没有定位到main入口 就IDA+OD分析
定位到相关汇编代码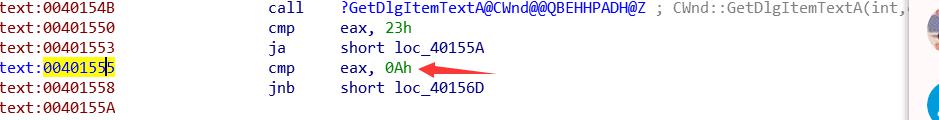
进行判断长度需要大于0Ah小于23h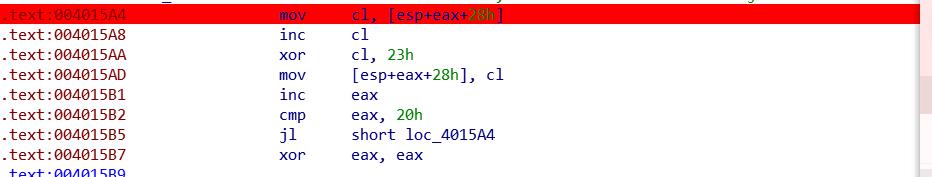
shift+F12 字符串搜索
定位到data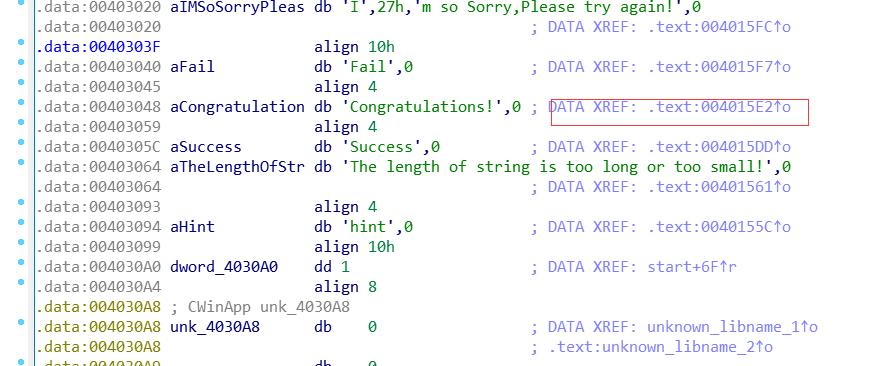
双击
DATA XREF 找到原引用位置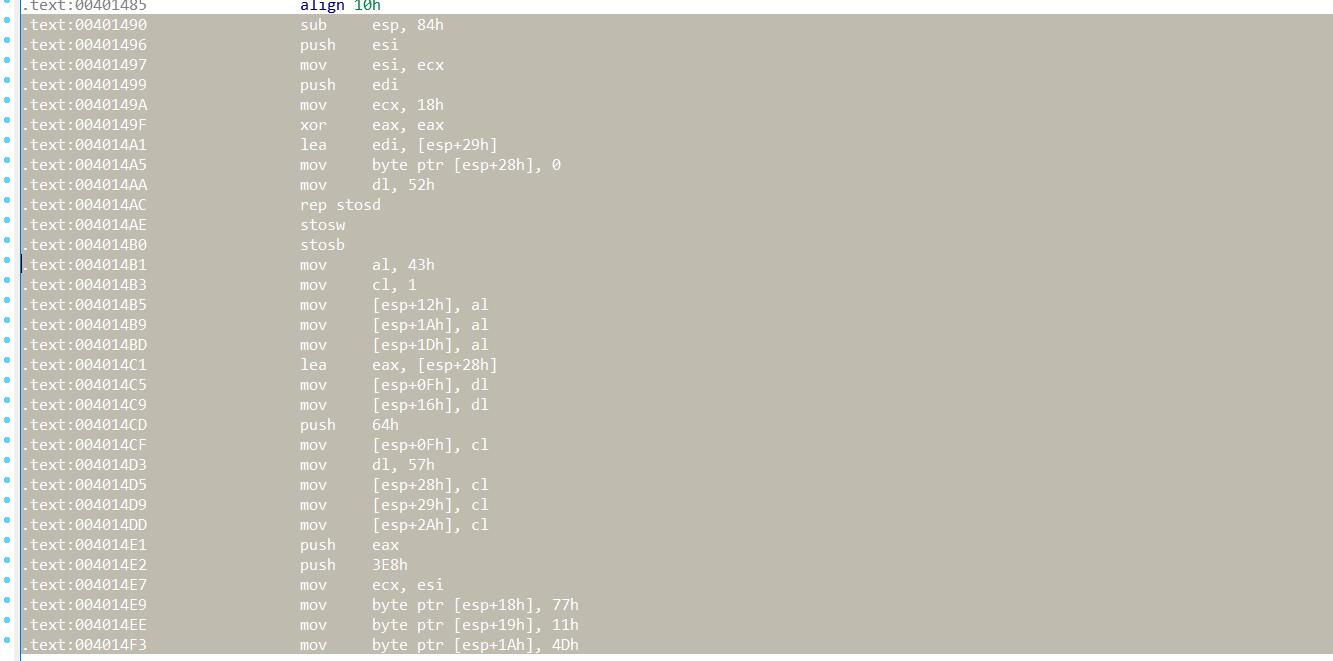
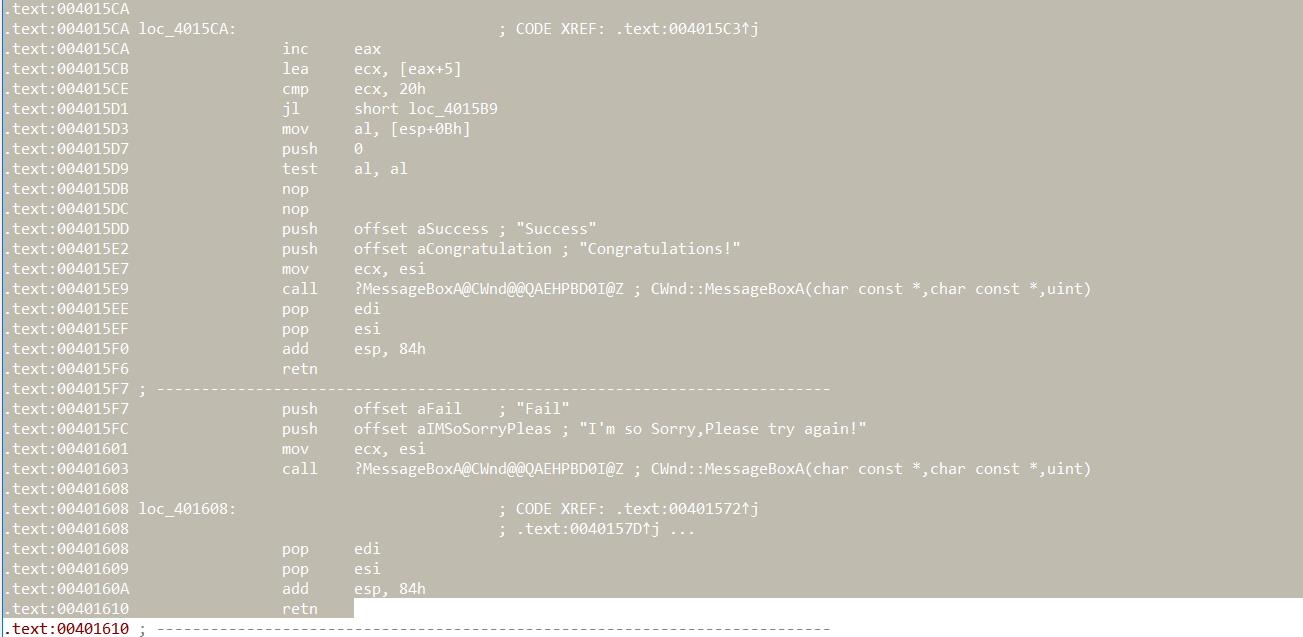
通过快捷键P create一个函数 得到主体函数
然后再通过F5转为C
unsigned int __thiscall sub_401490(CWnd *this)
{
CWnd *v1; // esi
unsigned int result; // eax
signed int v3; // eax
int v4; // eax
char v5; // [esp+Ch] [ebp-80h]
char v6; // [esp+Dh] [ebp-7Fh]
char v7; // [esp+Eh] [ebp-7Eh]
char v8; // [esp+Fh] [ebp-7Dh]
char v9; // [esp+10h] [ebp-7Ch]
char v10; // [esp+11h] [ebp-7Bh]
char v11; // [esp+12h] [ebp-7Ah]
char v12; // [esp+13h] [ebp-79h]
char v13; // [esp+14h] [ebp-78h]
char v14; // [esp+15h] [ebp-77h]
char v15; // [esp+16h] [ebp-76h]
char v16; // [esp+17h] [ebp-75h]
char v17; // [esp+18h] [ebp-74h]
char v18; // [esp+19h] [ebp-73h]
char v19; // [esp+1Ah] [ebp-72h]
char v20; // [esp+1Bh] [ebp-71h]
char v21; // [esp+1Ch] [ebp-70h]
char v22; // [esp+1Dh] [ebp-6Fh]
char v23; // [esp+1Eh] [ebp-6Eh]
char v24; // [esp+1Fh] [ebp-6Dh]
char v25; // [esp+20h] [ebp-6Ch]
char v26; // [esp+21h] [ebp-6Bh]
char v27; // [esp+22h] [ebp-6Ah]
char v28; // [esp+23h] [ebp-69h]
char v29; // [esp+24h] [ebp-68h]
char v30; // [esp+25h] [ebp-67h]
char v31; // [esp+26h] [ebp-66h]
char v32; // [esp+27h] [ebp-65h]
char v33; // [esp+28h] [ebp-64h]
char v34; // [esp+29h] [ebp-63h]
char v35; // [esp+2Ah] [ebp-62h]
char v36; // [esp+2Bh] [ebp-61h]
char v37; // [esp+2Ch] [ebp-60h]
char v38[27]; // [esp+2Dh] [ebp-5Fh]
char v39; // [esp+48h] [ebp-44h]
__int16 v40; // [esp+89h] [ebp-3h]
char v41; // [esp+8Bh] [ebp-1h]
v1 = this;
v33 = 0;
memset(&v34, 0, 0x60u);
v40 = 0;
v41 = 0;
v11 = 67;
v19 = 67;
v22 = 67;
v8 = 82;
v15 = 82;
v29 = 1;
v30 = 1;
v31 = 1;
v5 = 119;
v6 = 17;
v7 = 77;
v9 = 110;
v10 = 23;
v12 = 103;
v13 = 18;
v14 = 77;
v16 = 97;
v17 = 80;
v18 = 69;
v20 = 73;
v21 = 87;
v23 = 119;
v24 = 83;
v25 = 101;
v26 = 65;
v27 = 87;
v28 = 121;
v32 = 0;
result = CWnd::GetDlgItemTextA(this, 1000, &v33, 100);
if ( result > 0x23 || result < 0xA )
result = CWnd::MessageBoxA(v1, aTheLengthOfStr, aHint, 0);
if ( v33 == 66 && v34 == 85 && v36 == 84 && v35 == 80 && v37 == 123 && v39 == 125 )
{
v3 = 5;
do
{
*(&v33 + v3) = (*(&v33 + v3) + 1) ^ 0x23;
++v3;
}
while ( v3 < 32 );
v4 = 0;
do
{
v38[v4];
*(&v5 + v4++);
}
while ( v4 + 5 < 32 );
result = CWnd::MessageBoxA(v1, aCongratulation, aSuccess, 0);
}
return result;
}
修改调整数组
右键修改 重新F5得到清晰地代码 和密文
unsigned int __thiscall sub_401490(CWnd *this)
{
CWnd *v1; // esi
unsigned int result; // eax
signed int v3; // eax
int v4; // eax
char v5[64]; // [esp+Bh] [ebp-81h]
__int16 v6; // [esp+89h] [ebp-3h]
char v7; // [esp+8Bh] [ebp-1h]
v1 = this;
v5[29] = 0;
memset(&v5[30], 0, 0x60u);
v6 = 0;
v7 = 0;
v5[7] = 67;
v5[15] = 67;
v5[18] = 67;
v5[4] = 82;
v5[11] = 82;
v5[25] = 1;
v5[26] = 1;
v5[27] = 1;
v5[1] = 119;
v5[2] = 17;
v5[3] = 77;
v5[5] = 110;
v5[6] = 23;
v5[8] = 103;
v5[9] = 18;
v5[10] = 77;
v5[12] = 97;
v5[13] = 80;
v5[14] = 69;
v5[16] = 73;
v5[17] = 87;
v5[19] = 119;
v5[20] = 83;
v5[21] = 101;
v5[22] = 65;
v5[23] = 87;
v5[24] = 121;
v5[28] = 0;
result = CWnd::GetDlgItemTextA(this, 1000, &v5[29], 100);
if ( result > 0x23 || result < 0xA )
result = CWnd::MessageBoxA(v1, aTheLengthOfStr, aHint, 0);
if ( v5[29] == 66 && v5[30] == 85 && v5[32] == 84 && v5[31] == 80 && v5[33] == 123 && v5[61] == 125 )
{
v3 = 5;
do
{
v5[v3 + 29] = (v5[v3 + 29] + 1) ^ 0x23;
++v3;
}
while ( v3 < 32 );
v4 = 0;
do
{
v5[v4 + 34];
v5[v4++ + 1];
}
while ( v4 + 5 < 32 );
result = CWnd::MessageBoxA(v1, aCongratulation, aSuccess, 0);
}
return result;
}
得到密文之后可以进行 还原
Payload1
list=[119, 17, 77,82,110,23,67, 103,18,77,82,97,80,69,67,73,87,67,119,83,101,65,87,121,1,1,1,0]
str=""
for i in list:
str+=chr((i^0x23)-1)
print str
# BUPT{S1mpL3_C0mpAre_is_SoEasY!!!}
pyload2 无名师傅
intx(){
v6[6]=67;
v6[14]=67;
v6[17]=67;
v6[3]=82;
v6[10]=82;
v6[24]=1;
v6[25]=1;
v6[26]=1;
v6[0]=119;
v6[1]=17;
v6[2]=77;
v6[4]=110;
v6[5]=23;
v6[7]=103;
v6[8]=18;
v6[9]=77;
v6[11]=97;
v6[12]=80;
v6[13]=69;
v6[15]=73;
v6[16]='W';
v6[18]=119;
v6[19]=83;
v6[20]=101;
v6[21]='A';
v6[22]='W';
v6[23]='y';
for(inti=0;i<27;i++){
v6[i]^=0x23;
v6[i]=v6[i]-1;
}
printf(v6);
return0;
}
Re2
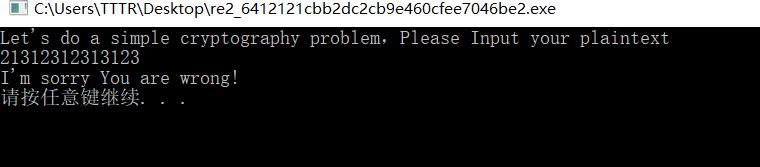
简单走流程 猜测应该和RE1思路相似 需要解密某加密
载入分析
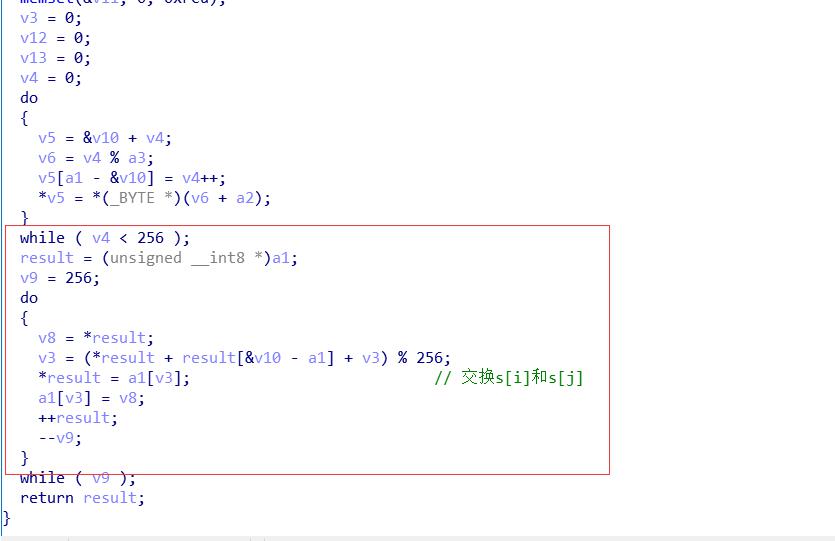
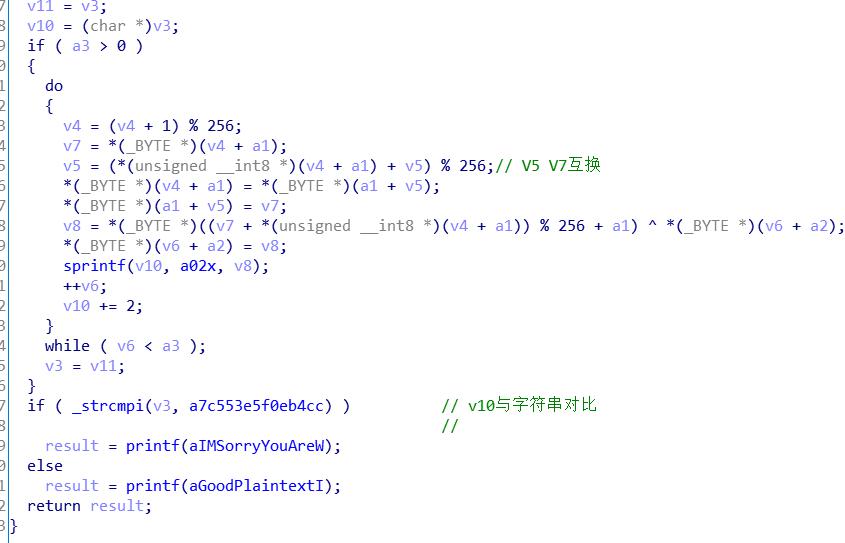
分析可以得出 加密方式为RC4加密
解密流程与加密流程相同
可以写的脚本跑出密文并走过第二个函数进行解密
# /usr/bin/python
# coding=utf-8
#dump初始化后的密钥流,做xor运算,拿到密钥流直接跑函数2出结果
data=[0x7C,0x55,0x3E,0x5F,0x0E,0xB4,0xCC,0xB9,0x77,0xBF,0x6B,0xD9,0x60,0xE0,0xB9,0x68,0xFB,0x11,0xCE,0xD2,0x15,0x4B,0x0E,0xB5,0xF7,0x3E,0x51,0xEE,0x51,0x4D,0x5A,0x9C,0x01,0xA0,0xC5,0x3A,0xD0,0x38]
s=[0x53,0x63,0x04,0xD5,0x11,0xFD,0xC2,0x3C,0x83,0x1D,0xB3,0x01,0xA0,0x0D,0x8E,0x95
,0xD3,0xF8,0x6F,0xE5,0xF1,0x94,0x6D,0xAA,0x05,0xCF,0x32,0x02,0xB1,0x35,0x0E,0x21
,0x8A,0x1F,0xA9,0x45,0xCB,0x4A,0xDD,0x1C,0x71,0x96,0x58,0x65,0xED,0x29,0x38,0xD6
,0x16,0xD9,0xAB,0xCC,0xE2,0x13,0x91,0x55,0xBC,0x43,0x4B,0x48,0xF3,0x3E,0xC8,0x6C
,0x0C,0x10,0x15,0xD1,0xB4,0x23,0x52,0x59,0x68,0xC5,0x7F,0x77,0xF2,0xA4,0x5D,0xF6
,0xFB,0x67,0xAC,0x24,0x72,0x8D,0x18,0x09,0x7C,0x8F,0xF4,0xB8,0x81,0xB0,0x44,0xDC
,0xA8,0xE0,0xC6,0xDA,0x00,0x8B,0x97,0x60,0xE3,0x14,0x9C,0x34,0xD7,0xD8,0x5B,0x3F
,0xFE,0x2E,0x33,0x06,0x7B,0xDE,0xC9,0xE7,0x9D,0x5E,0xF9,0x3B,0x75,0x5F,0x30,0xA2
,0xB6,0xA3,0x42,0xAE,0x85,0x37,0x28,0x89,0x66,0xBA,0x78,0x07,0xB9,0x1E,0x9A,0x2B
,0x1A,0x1B,0x39,0xEB,0x93,0x2C,0x64,0x6B,0x9B,0x47,0x80,0xEC,0xC0,0xA1,0x98,0xFC
,0xA6,0xE6,0xC3,0x62,0xAF,0x17,0x6A,0xB7,0x25,0x5A,0xE9,0x5C,0x54,0x0A,0x86,0xD4
,0xE4,0xF0,0x41,0x0F,0xB2,0x0B,0x7E,0x9F,0x4F,0xCE,0xF5,0x99,0xB5,0xC4,0x4D,0xA7
,0xCA,0x19,0x12,0xE1,0x8C,0x36,0xDF,0xE8,0x6E,0x88,0x22,0xD2,0x46,0x26,0xD0,0x03
,0xC1,0xC7,0x08,0x31,0xBB,0x2A,0x7D,0x3A,0xEF,0x4C,0xBD,0xEE,0xFA,0x70,0x50,0xFF
,0xCD,0x20,0x51,0x40,0x57,0xA5,0x82,0x9E,0x69,0x56,0x2D,0x84,0x73,0x74,0x4E,0xBE
,0x2F,0x76,0x7A,0x90,0x92,0xDB,0xF7,0xAD,0x3D,0x87,0x49,0xBF,0xEA,0x79,0x61,0x27]
a1 = 0
a2 = 0
temp = 0
str=""
for i in range(38):
a1=(a1+1)%256
a2=(a2+s[a1])%256
temp=s[a1]
s[a1]=s[a2]
s[a2]=temp
temp=(s[a1]+s[a2])%256
data[i]^=s[temp]
str+=chr(data[i])
print str
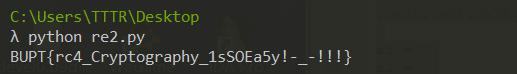
运行即可跑出flag
#BUPT{rc4_Cryptography_1sSOEa5y!-_-!!!}
Re3
2333太菜了比赛时间内没做出来0.0